
An Iranian Advanced Persistent Threat (APT) actor likely affiliated with the Ministry of Information and Security (MOIS) is now acting as an initial access enabler providing remote access to target networks.
Google-owned Mandiant tracks the activity cluster under the name UNC1860which he said bears similarities to intrusion kits pursued by Microsoft, Cisco Talos and Check Point as Storm-0861 (formerly DEV-0861), ShroudedSnooper and Scarred Manticore respectively.
“A key feature of the UNC1860 is its collection of specialized tools and passive doors that […] supports multiple objectives, including its role as a likely initial access provider and its ability to gain persistent access to high-priority networks such as those in the Middle East government and telecommunications space,” the company said.
The group first came to light in July 2022 in connection with destructive cyber attacks targeting Albania with a ransomware strain called ROADSWEEP, the CHIMNEYSWEEP backdoor, and a ZEROCLEAR wiper variant (aka Cl Wiper), with subsequent intrusions in Albania and Israel using new wipers called No-Justice and BiBi (aka BABYWIPER).
Mandiant described UNC1860 as a “formidable threat actor” that maintains an arsenal of passive backdoors that are designed to gain footholds in victim networks and set up long-term access without attracting attention.
Among these tools are two GUI-operated malware controllers, tracked as TEMPLEPLAY and VIROGREEN, which are said to provide other MOIS-related threat actors with remote access to the victim’s environments using Remote Desktop Protocol (RDP).
Specifically, these controllers are designed to provide third-party operators with an interface that provides instructions on how custom payloads could be deployed and post-exploit activities, such as internal scanning, could be performed on the target network.

Mandiant said it identified overlaps between UNC1860 and APT34 (aka Hazel Sandstorm, Helix Kitten and OilRig) in that organizations compromised by the latter in 2019 and 2020 were previously infiltrated by UNC1860 and vice versa. In addition, both groups have been observed pivoting to targets based in Iraq, as Check Point recently pointed out.
Attack chains involve leveraging initial access gained by opportunistically exploiting vulnerable Internet-facing servers to launch web shells and droppers such as STAYSHANTE and SASHEYAWAY, the latter leading to the execution of implants such as TEMPLEDOOR, FACEFACE and SPARKLOAD , which are embedded. within it.
“VIROGREEN is a custom framework used to exploit SharePoint servers vulnerable to CVE-2019-0604,” the researchers said, adding that it controls STAYSHANTE, along with a backdoor called BASEWALK.
“The framework provides post-exploitation capabilities including […] control of post-exploit payloads, backdoors (including the STAYSHANTE web shell and the BASEWALK backdoor) and tasks; control of a compatible agent regardless of how the agent was implanted; and executing commands and uploading/downloading files.
TEMPLEPLAY (internally called Http Client), in turn, serves as a .NET-based controller for TEMPLEDOOR. It supports backdoor instructions for executing commands via cmd.exe, uploading/downloading files to and from the infected host, and proxying to a target server.
The adversary is believed to have a diverse collection of passive tools and backdoors in his possession that align with his initial goals of access, lateral movement, and intelligence gathering.
Some of the other note tools documented by Mandiant are listed below –
- OATBOAT, a loader that loads and executes shellcode payloads
- TOFUDRV, a malicious Windows driver that overlaps with WINTAPIX
- TOFULOAD, a passive implant that uses undocumented input/output control (IOCTL) commands for communication
- TEMPLEDROP, a repurposed version of an Iranian antivirus software Windows file system filter driver called Sheed AV, which is used to protect the files it deploys from modification
- TEMPLELOCK, a .NET defense evasion utility that is capable of destroying the Windows Event Log service
- TUNNELBOI, a network controller capable of establishing a connection to a remote host and handling RDP connections
“As tensions continue to ebb and flow in the Middle East, we believe this actor’s ability to gain initial access to target environments is a valuable asset to the Iranian cyber ecosystem that can be exploited to meet evolving objectives as needs evolve.” change,” researchers Stav Shulman. , said Matan Mimran, Sarah Bock and Mark Lechtik.
The development comes as the US government revealed ongoing attempts by Iranian threat actors to influence and undermine the upcoming US election by stealing non-public materials from former President Donald Trump’s campaign.
“Malicious Iranian cyber actors in late June and early July sent unsolicited emails to individuals then associated with President Biden’s campaign that contained an excerpt of stolen, non-public materials from former President Trump’s campaign as text in the emails” , the government said.

“There is currently no information to indicate that those recipients have responded. In addition, Iranian cyber actors continued their efforts since June to send stolen, non-public material associated with former President Trump’s campaign to US media organizations.”
Iran’s increase in its cyber operations against its perceived rivals also comes at a time when the country has become increasingly active in the Middle East region.
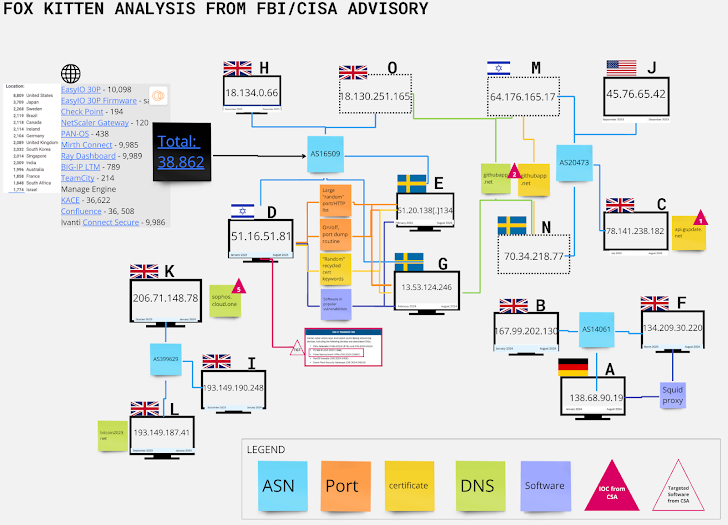
Late last month, the US Cybersecurity and Infrastructure Security Agency (CISA) warned that Iranian APT Lemon Sandstorm (aka Fox Kitten) has been carrying out ransomware attacks by clandestinely partnering with NoEscape, RansomHouse and BlackCat (aka ALPHV) crews.
Censys’ analysis of the hacking group’s attack infrastructure has since revealed other currently active hosts likely to be part of it based on commonalities based on geolocation, autonomous system numbers (ASNs), and identical port patterns and digital certificates.
“Despite attempts at obfuscation, hijacking and randomization, people still need to instantiate, operate and decommission digital infrastructure,” said Censys’ Matt Lembright.
“Those people, even if they rely on technology to create randomization, will almost always follow some kind of pattern, whether it’s similar autonomous systems, geographic locations, hosting providers, software, port distributions, or certificate characteristics. “
#Iranian #APT #UNC1860 #linked #MOIS #facilitates #cyber #intrusions #Middle #East
